The content below is taken from the original ( BlackBerry and Amazon team up to make connected cars more secure), to continue reading please visit the site. Remember to respect the Author & Copyright.

The content below is taken from the original ( BlackBerry and Amazon team up to make connected cars more secure), to continue reading please visit the site. Remember to respect the Author & Copyright.

The content below is taken from the original ( Office 365 Has Changed Enormously Since 2011), to continue reading please visit the site. Remember to respect the Author & Copyright.

At the start of the decade, Microsoft’s cloud offering was the deservedly maligned Business Online Productivity Services (BPOS: a name only its inventor could love). BPOS was unreliable and didn’t work particularly well. Because BPOS used software designed for on-premises use, it struggled to cope with cloud operations.
Thankfully, Microsoft transformed its cloud office system with the introduction of Office 365 on 28 June 2011. After a slow start, Office 365 has gathered pace and overcome G Suite, its major rival to become the leader in cloud office systems. In this article, I look back at the roots of Office 365 and discuss the three major issues that initially spooked customers about the cloud. In the next, I describe some of the Office 365 successes and failures in the last decade.
Looking back from today’s perspective, it’s hard to remember just how limited Office 365 was in 2011. The software was based on the 2010 on-premises versions of Exchange, SharePoint, and Lync knitted together with a licensing and administration portal. Microsoft’s engineering groups were still working out how to transform the on-premises software to work at cloud scale, and it’s fair to say that this process didn’t finish until a few years later.
The Office 365 ecosystem also needed to be built out. Where Microsoft had three datacenter regions in 2011, it now delivers Office 365 services from 17, a development that resolved the initial fears some customers had about data sovereignty. The datacenters are connected by a dark fiber network linked to a huge set of local connection points to make it easy for users to work no matter where they are. Tenants can run a multi-geo configuration for Exchange Online, SharePoint Online, and OneDrive for Business, and Microsoft is steadily moving app data closer to customers as it builds out its datacenters.
The Office 365 datacenters store enormous amounts of user data. Microsoft has increased quotas for Exchange Online and SharePoint Online (for instance, the standard enterprise mailbox is now 100 GB instead of 25 GB) and many ISVs make products to help customers move data from on-premises apps into the cloud. We’re now at the point where the majority of Exchange and SharePoint activity is cloud-based, and the number of on-premises customers for Office servers continues to fall year over year.
At launch, Microsoft offered Office 365 plans for kiosk (now frontline) and enterprise workers. A set of slides posted by Mary-Jo Foley includes how Microsoft positioned Office 365 enterprise (Figure 1) when they started to talk to customers about the new cloud office suite.
 Figure 1: Positioning Office 365 Enterprise in 2011
Figure 1: Positioning Office 365 Enterprise in 2011Access to Blackberry Enterprise Server was important in 2011, but the list of advantages Microsoft touted for Office 365 was short (possibly because no one realizes how good cloud office could be then). What’s interesting is the pricing Microsoft set for Office 365 (Figure 2). Plan E3 was $24/month then, and it’s $20/month now.
 Figure 2: Costs of Office 365 Enterprise Plans in 2011
Figure 2: Costs of Office 365 Enterprise Plans in 2011The point here is that companies were scared that Microsoft would get them onto Office 365 and then hike the prices, something that simply hasn’t happened. In fact, Office 365 is a relative bargain now because all its plans include more and better functionality than they did in 2011.
Instead of bumping plan prices up, Microsoft has concentrated on growing the numbers of Office 365 accounts and increasing the Average Revenue Per User (APRU) by upselling add-ons and higher-priced plans to customers or moving them to Microsoft 365. Office 365 now has over 200 million monthly active users and has grown at between 3 and 4 million users per month since 2015 and Office 365 is responsible for the bulk of Microsoft’s cloud revenues, so their tactics have worked.
Being price-gouged was one customer fear in 2011. Not trusting cloud services to deliver highly available services was another. Microsoft launched Office 365 with a financially-backed guarantee that the 99.9% Service Level Agreement (SLA) would be reached. Since then, Microsoft hasn’t had to pay out all that often. In fact, I can only remember one instance in September 2011 when the infrastructure was still maturing, and Microsoft’s automated datacenter management processes were not as extensive or as tightly controlled as they are today.
Given the size of Office 365, it’s inevitable that something is going wrong at any time you care to look. But the number of tenants, distribution across multiple regions, and the way the software is deployed and managed mean that it’s a rare incident that comes anywhere close to budging the SLA needle (an example of one that did is the MFA outages in 2018). This has been the case for several years, which begs the question whether the Office 365 SLA is relevant today.
A perceived lack of security was the last of the triple whammy used to justify not going to the cloud. When you think about it, this is a laughable notion for most organizations because they don’t possess the experience, knowledge, skills, and resources that Microsoft dedicates to protecting Office 365 against a world of threat. Microsoft says that 3,500 security professionals protect customer data, all of whom probably know more about security than I do. I lost the fear of having my data in the cloud a long time ago and like the idea that dedicated personnel are responsible for protecting the service.
Attacks happen all the time, but I can’t recall reports of any Office 365 tenant being penetrated solely because of a Microsoft failure. Maybe no-one highlights big security breaches because they do not want to embarrass their company, or I am just not listening. In whatever case, it’s still true that the responsibility for basic security remains with tenants. In this respect, the low percentage of sensitive Office 365 accounts protected with multi-factor authentication is an ongoing scandal.
Microsoft’s commercial cloud products have grown to an annual revenue run rate of well over $40 billion. Office 365 is a big part of that success. To its credit, Microsoft has overcome many technical, organizational, and business challenges to attain that success. The trick now is to keep customers happy, ahead of the competition, and deliver the same quality of service over the next decade.
The post Office 365 Has Changed Enormously Since 2011 appeared first on Petri.
The content below is taken from the original ( Your excess server resources are wanted in the cloud), to continue reading please visit the site. Remember to respect the Author & Copyright.
Although not a new concept, we are now looking at the opportunity for those who have private servers with excess capacity to rent that capacity to a cloud service provider that can dole out those compute and storage systems on demand to anyone who needs them.
If you’re thinking ride-sharing for servers, you’re not far off. In this scenario the cloud service provider is really just a broker sitting between those needing cloud services and those who have servers that can be shared. You may be leveraging servers that have excess capacity in Las Vegas on Monday and perhaps servers in London on Tuesday. You don’t care since you’re abstracted away from the physical servers, not even knowing location and true ownership.
The content below is taken from the original ( Behold Schrödinger’s Y2K, when software went all quantum), to continue reading please visit the site. Remember to respect the Author & Copyright.
Y2K Welcome to Y2K, The Register’s collection of ramblings from readers tasked with dealing with what almost happened – but didn’t – during those halcyon days of two decades past.…
The content below is taken from the original ( 36C3: SIM Card Technology From A to Z), to continue reading please visit the site. Remember to respect the Author & Copyright.
SIM cards are all around us, and with the continuing growth of the Internet of Things, spawning technologies like NB-IoT, this might as well be very literal soon. But what do we really know about them, their internal structure, and their communication protocols? And by extension, their security? To shine some light on these questions, open source and mobile device titan [LaForge] gave an introductory talk about SIM card technologies at the 36C3 in Leipzig, Germany.
Starting with a brief history lesson on the early days of cellular networks based on the German C-Netz, and the origin of the SIM card itself, [LaForge] goes through the main specification and technology parts of each following generation from 2G to 5G. Covering the physical basics, I/O interfaces, communication protocols, and the file system located on the SIM card, you’ll get the answer to “what on Earth is PIN2 for?” along the way.
Of course, a talk like this, on a CCC event, wouldn’t be complete without a deep and critical look at the security side as well. Considering how over-the-air updates on both software and — thanks to mostly running Java nowadays — feature side are more and more common, there certainly is something to look at.
The content below is taken from the original ( Image Sensor from Discrete Parts Delivers Glorious 1-Kilopixel Images), to continue reading please visit the site. Remember to respect the Author & Copyright.
Chances are pretty good that you have at least one digital image sensor somewhere close to you at this moment, likely within arm’s reach. The ubiquity of digital cameras is due to how cheap these sensors have become, and how easy they are to integrate into all sorts of devices. So why in the world would someone want to build an image sensor from discrete parts that’s 12,000 times worse than the average smartphone camera? Because, why not?
[Sean Hodgins] originally started this project as a digital pinhole camera, which is why it was called “digiObscura.” The idea was to build a 32×32 array of photosensors and focus light on it using only a pinhole, but that proved optically difficult as the small aperture greatly reduced the amount of light striking the array. The sensor, though, is where the interesting stuff is. [Sean] soldered 1,024 ALS-PT19 surface-mount phototransistors to the custom PCB along with two 32-bit analog multiplexers. The multiplexers are driven by a microcontroller to select each pixel in turn, one row and one column at a time. It takes a full five seconds to scan the array, so taking a picture hearkens back to the long exposures common in the early days of photography. And sure, it’s only a 1-kilopixel image, but it works.
[Sean] has had this project cooking for a while – in fact, the multiplexers he used for the camera came up as a separate project back in 2018. We’re glad to see that he got the rest built, even with the recycled lens he used. One wonders how a 3D-printed lens would work in front of that sensor.
The content below is taken from the original ( Microsoft Plans to Disable SMTP AUTH in Exchange Online), to continue reading please visit the site. Remember to respect the Author & Copyright.

There are two things certain in Office 365 security. First, multi-factor authentication (MFA) is a very good thing and will block 99.9% of account compromise attacks. Second, basic authentication is an invitation for an attacker to probe for weakly secured accounts using multiple connection protections, including SMTP.
The message about the need to secure accounts with MFA is slowly getting through. Too slowly, but at least we see some progress. Eliminating basic authentication is high on the agenda of the Exchange Online team. They own protocols like IMAP4, POP3, SMTP, and so on. The introduction of protocol authentication policies in 2018 was a good step forward. Tenant administrators can deploy authentication policies to restrict the number of connection protocols that can be used with basic authentication for mailboxes.
In March 2018, Microsoft flagged the need for tenants to move away from basic authentication by announcing that support for basic authentication for Exchange Web Services will cease on October 13, 2020. This means that anyone using code built with EWS must upgrade to OAuth 2.0 and use that for authentication. EWS has a limited lifespan and it is a good idea at this point to consider moving code to a Graph-based implementation.
Microsoft then increased the pace in September 2019 by announcing that they will turn off basic authentication for Exchange ActiveSync (EAS), POP3, IMAP4 and Remote PowerShell in October 2020. Microsoft has already enabled OAuth (modern) authentication for EAS and is doing so for POP3 and IMAP4 to give tenants a path forward. Those using Remote PowerShell can connect using the Exchange Online Management module, which only supports OAuth and includes both the old (Remote PowerShell) and new (REST-based) cmdlets.
An interesting detail in the announcement was:
“this change does not affect SMTP AUTH – we will continue supporting Basic Authentication for the time being. There is a huge number of devices and appliances that use SMTP for sending mail, and so we’re not including SMTP in this change – though we are working on ways to further secure SMTP AUTH”
This note is a sober realization that many multifunction devices are configured to connect to Exchange Online to send messages via SMTP (authenticated submission) when printing or copying jobs complete or scripts run to report on different operational conditions. Retrofitting devices to use OAuth is a challenging proposition, so Microsoft is choosing to leave the situation as is for SMTP for now.
Two months later, Microsoft shared some extra detail about their direction to control SMTP authenticated submissions at the Microsoft Ignite 2019 conference. Microsoft noted that the ability to disable this feature on a per-user basis via PowerShell and the Office 365 Admin Center (Figure 1) and at the organization level already exists.
 Figure 1:Using the Office 365 Admin Center to disable SMTP authenticated submissions for a mailbox (image credit: Tony Redmond)
Figure 1:Using the Office 365 Admin Center to disable SMTP authenticated submissions for a mailbox (image credit: Tony Redmond)To disable SMTP authenticated submissions for all mailboxes in a tenant with PowerShell, run this command:
Get-CasMailbox | ? {$_.SmtpClientAuthenticationDisabled -eq $Null -or $_.SmtpClientAuthenticationDisabled -eq $False }| Set-CasMailbox –SmtpClientAuthenticationDisabled $True
When a mailbox is blocked from SMTP authenticated submissions, it can’t be used to submit email to Exchange Online by running the PowerShell Send-Message cmdlet (using SMTP AUTH client submission). Attempts to send messages by an unauthorized account see this error:
Send-MailMessage : The SMTP server requires a secure connection or the client was not authenticated. The server response was: 5.7.57 SMTP; Client was not authenticated to send anonymous mail during MAIL FROM
As it’s unlikely that any tenant can stop using PowerShell to send email, they should instead seek to minimize the set of mailboxes that can submit email via PowerShell.
Microsoft also said that:
“…we’re going to better secure this protocol (disable it) by default, first for new organizations onboarding onto Office 365, then later for tenants with no SMTP authenticated submission usage. We also expect in the future to deliver more tools, reports, and optics to help email admins gain better insight into SMTP authenticated submission usage in their organizations.”
This statement underlines the seriousness of Microsoft’s intent to reduce the attack surface available through SMTP. Soon, new Office 365 tenants will not be able to use SMTP authenticated submission for devices or users. Afterwards, Microsoft will move to disable SMTP authenticated submission for tenants that don’t use the feature. Both these steps make sense. After all, if you don’t use something or have never used something, you won’t miss that thing when it is taken away.
Microsoft clearly intends that tenants should protect themselves by limiting SMTP authenticated submissions to as small a set of accounts as possible. What Microsoft is not saying (yet) is when they will disable SMTP authenticated submissions across Office 365. In fact, this probably won’t happen because of likely customer pushback. Apart from devices set up to send email, there are too many PowerShell scripts in use that call the Send-Message cmdlet to send email for Microsoft to be able to disable SMTP authenticated submissions completely. At least, not in the short term.
What I think is more likely is that Microsoft will figure out how best to secure SMTP submissions for devices and scripts in a way that’s easy for tenants to adopt. When they do, I expect Microsoft to set a deadline for tenants to upgrade devices and scripts to use whatever the new mechanism is. Hopefully that limit is reasonable enough to give tenants enough time to do the necessary work.
Tenants should understand that Microsoft is moving in this direction to secure tenant data and operations. With that in mind, it’s a good idea to create an inventory of devices and scripts in use today so that tenants know what work might need to be done in the future. Insecure connectivity protocols are on their way out. The only question now is when this will happen.
The post Microsoft Plans to Disable SMTP AUTH in Exchange Online appeared first on Petri.
The content below is taken from the original ( Update: ChromePass v1.47), to continue reading please visit the site. Remember to respect the Author & Copyright.
Added new file format to export the passwords: Chrome CSV File. It’s the same file format that Chrome Web browser exports the passwords from chrome://settings/passwords
The content below is taken from the original ( How to write your own annual cycling training plan), to continue reading please visit the site. Remember to respect the Author & Copyright.

January is the month of new resolutions. However, without a plan most new ambitions won’t go much further than the Facebook meme stage. ‘A goal is a dream with a plan’, or so such memes might proclaim (the original quote comes from motivational speaker, Greg Reid, we believe). There’s truth in that – provided your dream […]
The content below is taken from the original ( Track suspicious login activities in your tenant!!), to continue reading please visit the site. Remember to respect the Author & Copyright.
submitted by /u/Kathy_Cooper1012 to r/usefulscripts
[link] [comments]
The content below is taken from the original ( The Ultimate Guide to Building REST APIs with PowerShell), to continue reading please visit the site. Remember to respect the Author & Copyright.
submitted by /u/l33t_d0nut to r/PowerShell
[link] [comments]
The content below is taken from the original ( IBM’s cobalt-free EV battery uses materials extracted from seawater), to continue reading please visit the site. Remember to respect the Author & Copyright.

The content below is taken from the original ( Carbon will print parts for Lamborghini’s Sián FKP 37 hybrid sports car), to continue reading please visit the site. Remember to respect the Author & Copyright.
Carbon today announced the expansion of its partnership with Lamborghini. The white-hot 3D-printing startup will manufacture central and lateral dashboard air vents for the carmaker’s Sián FKP hybrid sports car.
The move follows the deal announced earlier this year that found Carbon printing a fuel cap and an air duct clip for Lamborghini’s Urus SVU. Baby steps, honestly, but important ones nonetheless. Lamborghini follows in Ford’s footsteps with the Carbon partnership.

It’s clear that automotive companies are interested in introducing custom 3D-printed parts, and Carbon has proven a degree of scalability with partnerships with companies like Adidas. It was clear from the outset, however, that such a deal would need to begin with smaller pieces, before injection molding could be replaced outright.
According to Carbon, the addition of 3D printing reduced the time to production by 12 weeks over more traditional manufacturing tools. The units were put through the paces, too, subjecting the EPX 82 material to a battery of stress tests.
“With the Carbon Digital Manufacturing Platform, we were able to go from an initial concept to showing the final part on a show car in only three weeks, passing through many different design iterations to get the best result,” Lamborghini CTO Maurizio Reggiani said in a release. “Just three months later, we were able to move into production.”
In a recent conversation with TechCrunch, Carbon’s new CEO Ellen Kullman noted the company’s push toward developing existing partnerships before rushing into new ones. “[T]here’s a lot of building out to do of what we’ve already committed to,” she told the site.
The content below is taken from the original ( Admin Essentials: know your options for Modern Enterprise Browser Management), to continue reading please visit the site. Remember to respect the Author & Copyright.
As more applications move to the cloud, without question, the browser is becoming more important. As an IT admin, you have to manage and ensure working in the cloud is seamless for your users.
Here at Google, the Chrome Browser enterprise team has been working hard to open up new and easier management options to help you do just that. For example, we’re expanding existing Group Policy templates within Active Directory, enabling support for applying policies to Mac, and even providing a central console to help you manage Chrome Browser from the cloud.
When it comes to management, it’s important to take a close look at options to see what works best for you, your team and your endpoints. In this post, we’ll take a look at some of the many management options available in Chrome Browser today.
1. Chrome Browser Cloud Management
Earlier this year, we announced the availability of Chrome Browser Cloud Management, which makes it possible to centrally enroll and manage browsers, as well as gain visibility into your browser deployments, right from within the Google Admin console. You can unify the management of Chrome Browser across Windows, Mac and Linux environments, and get a single view into extension, policies, versions and more. Check out our website to learn how to get started or watch this demo video:
2. Microsoft Endpoint Manager
Another option to consider is to manage Chrome Browser through Microsoft Intune (now part of Microsoft Endpoint Manager) on your Windows 10 devices, where you can use the same useful Chrome Browser ADMX templates. You can define and apply rules for hundreds of policies right from within the Microsoft management console. One benefit to this option is that if you are using Microsoft System Center Configuration Manager to manage Chrome’s installation and/or updates, it can be easier to handle from the same view. This is especially helpful if you are starting to use Microsoft Intune to manage your mobile devices and mobile apps.
You can also manage the popular Legacy Browser Supportcapability right from the Intune console, pre-defining sites to open in alternate browser outside of Chrome. This capability is used to help seamlessly redirect your users to legacy browsers when older web apps are unable to run in a modern browser.
3. VMware Workspace ONE Unified Endpoint Management
If your organization uses Workspace ONE as a primary management tool, you can also manage your Chrome Browser instances within the Unified Endpoint Management console for both desktop and Androiddevices. Just apply Chrome’s ADMX templates and push policies out to your Windows machines. Since Chrome Browser is optimized for virtual environments, you can determine and apply settings across your physical and virtual desktops using Chrome’s policy templates.
With Workspace ONE, you can use a single tool to manage Chrome Browser in your Windows environments, as well as provide basic management on your users mobile devices, without impacting a user’s personal Chrome app installation, if they have one. And for Workspace ONE customers with Chrome OS in their environments, they can also centrally manage their Chrome devices from one panel.
Manage Chrome your Way
Chrome continues to invest in making it possible for you and your team to use existing technology to manage browsers. In the near future, we plan to expand the capabilities available in Chrome Browser Cloud Management and to provide even more options.
If your enterprise is exploring different management options for endpoints, consider the browser as part of that conversation. With so many options available, managing your user’s Chrome Browser has never been so flexible. Learn more on our website.
The content below is taken from the original ( Roland’s Alexa-powered keyboard is available for $500), to continue reading please visit the site. Remember to respect the Author & Copyright.

The content below is taken from the original ( How to Install Office Web apps as PWA on Windows 10), to continue reading please visit the site. Remember to respect the Author & Copyright.

 In today’s post, we will show you how you can install Office Web Apps (Word, Excel, PowerPoint, Outlook) on Windows 10 as Progressive Web Apps for a more traditional experience. PWAs are just a combination of a traditional browser and […]
In today’s post, we will show you how you can install Office Web Apps (Word, Excel, PowerPoint, Outlook) on Windows 10 as Progressive Web Apps for a more traditional experience. PWAs are just a combination of a traditional browser and […]
This post How to Install Office Web apps as PWA on Windows 10 is from TheWindowsClub.com.
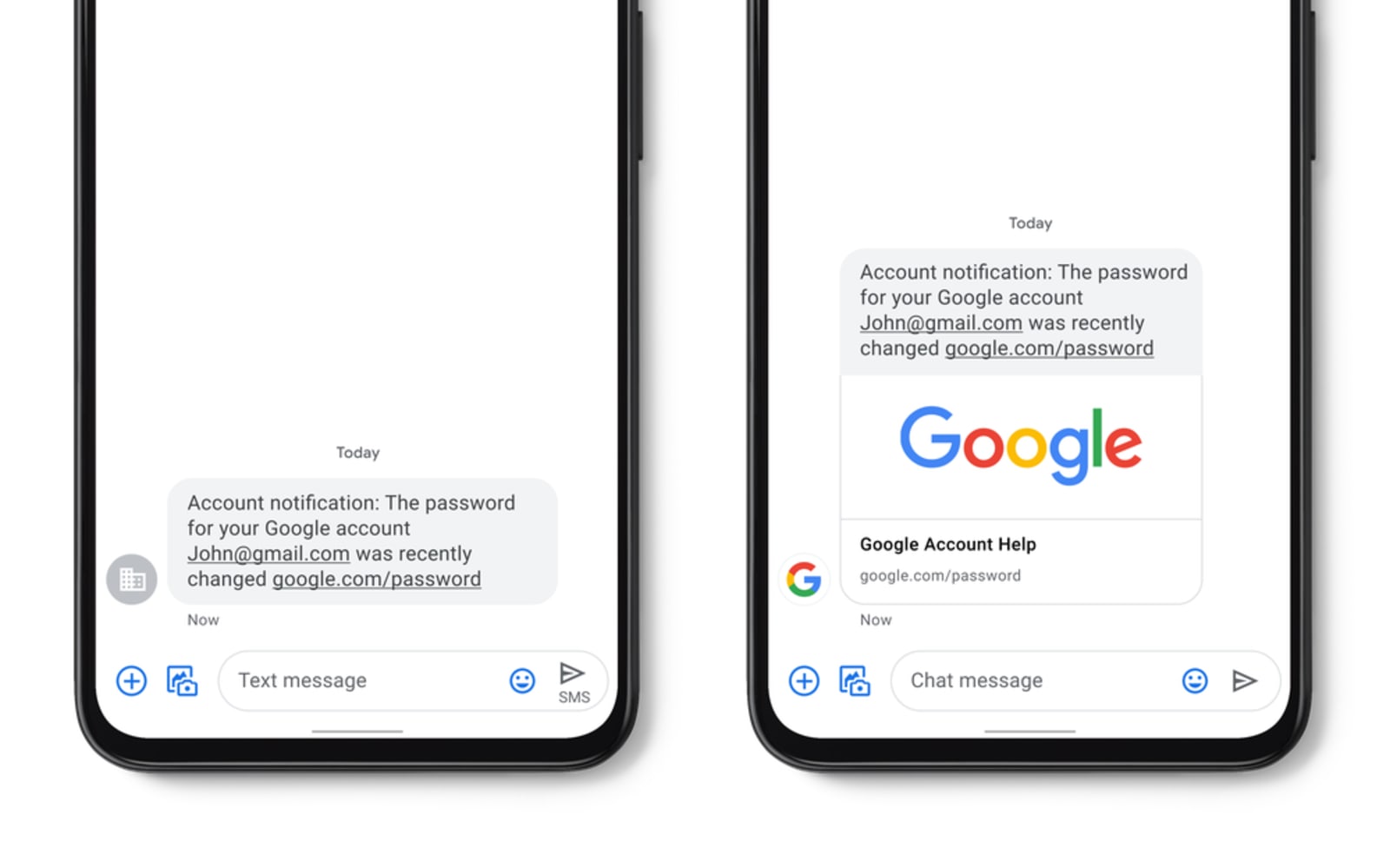
The content below is taken from the original ( Google adds spam detection and verified business SMS to Messages), to continue reading please visit the site. Remember to respect the Author & Copyright.
The content below is taken from the original ( The next Xbox is called Series X and it looks like a PC tower), to continue reading please visit the site. Remember to respect the Author & Copyright.

gave a glimpse of the next Xbox and revealed the console’s its name: Xbox Series X. Previously known as Project Scarlett, the next-generation Xbox resembles a PC tower and it arrives holida… holiday 2020.
The content below is taken from the original ( in /r/ YouShouldKnow), to continue reading please visit the site. Remember to respect the Author & Copyright.
Drag-drop youtube links to VLC and it will play them without ads and with the great player features included in VLC
The content below is taken from the original ( Google Chrome will check for leaked credentials every time you sign in anywhere), to continue reading please visit the site. Remember to respect the Author & Copyright.
A new feature in Google’s Chrome browser will warn you if your username and password matches a known combination in a security data breach every time you type credentials into any website.…
The content below is taken from the original ( Microsoft’s Offering a ‘Free’ Cyber Security Checkup to SMBs), to continue reading please visit the site. Remember to respect the Author & Copyright.


In about a month from now, Windows 7 will reach its end of support timeline which means unless you are willing to pay up, you are going to be sitting on the sidelines when it comes to securing your environment. While large companies are likely able to swallow the fees associated with extended support, the most vulnerable group will be the small and medium business (SMB).
An SMB is typically a company that is 300 or fewer employees and according to Microsoft, these companies are targeted more than half the time when it comes to cyber-attacks. Why? It’s primarily because they have fewer resources to help secure their environments and as we all know, IT shops typically have budgets that are stretched to the limits as they do not grow at the same rate as the rest of the organization.
Back at Ignite 2019, I was able to sit down with Brad Anderson, Corp. Vice President, Microsoft 365, and while we talked about many aspects of Microsoft 365, one point that he drilled down on was that, candidly, the company needed to do more to help address the smaller business of the world and not just the enterprise operations.
Today, Microsoft is announcing a new collaboration with AXA XL and Slice Labs to offer free cybersecurity health checks and support AXA XL’s provision of cyber insurance for qualified customers that use Microsoft 365 Business, Office 365 Business, and Office 365 Business Premium.
The idea here is simple, for customers willing to move to or are already using one of the above services, you can receive a ‘free’ audit of your operations and also have access to cybersecurity insurance as well. And at first, I was skeptical of this but I think there is actual merit to this offer.
Primarily because this comes as a benefit to already using those services, not as a carrot to get you to jump into new hoops. And for the SMBs of the world where budgets are tight, taking advantage of an external audit of your environment is a serious proposition. Of course, this is also useful to customers who may be on the fence about subscribing to these services too, as it may get them to finally sign up.
For many organizations, security is something you deal with to check a few boxes of compliance and is often only thought about after a breach has occurred. But the truth is that in a world where your operational availability is closely linked to your reputation, security needs to be significantly more proactive, than reactive.
What Microsoft is trying to offer here is to move your needle slightly more towards the proactive side of the equation but keep in mind, nothing is truly free.
The post Microsoft’s Offering a ‘Free’ Cyber Security Checkup to SMBs appeared first on Petri.
The content below is taken from the original ( Uber can find a ride to carry your skis in 23 regions), to continue reading please visit the site. Remember to respect the Author & Copyright.

The content below is taken from the original ( Introducing E2, new cost-optimized general purpose VMs for Google Compute Engine), to continue reading please visit the site. Remember to respect the Author & Copyright.
General-purpose virtual machines are the workhorses of cloud applications. Today, we’re excited to announce our E2 family of VMs for Google Compute Engine featuring dynamic resource management to deliver reliable and sustained performance, flexible configurations, and the best total cost of ownership of any of our VMs.
Now in beta, E2 VMs offer similar performance to comparable N1 configurations, providing:
Lower TCO: 31% savings compared to N1, offering the lowest total cost of ownership of any VM in Google Cloud.
Consistent performance: Your VMs get reliable and sustained performance at a consistent low price point. Unlike comparable options from other cloud providers, E2 VMs can sustain high CPU load without artificial throttling or complicated pricing.
Flexibility: You can tailor your E2 instance with up to 16 vCPUs and 128 GB of memory. At the same time, you can provision only only pay for the resources that you need with 15 new predefined configurations or the ability to use custom machine types.
Since E2 VMs are based on industry-standard x86 chips from Intel and AMD, you don’t need to change your code or recompile to take advantage of this price-performance.
E2 VMs are a great fit for a broad range of workloads including web servers, business-critical applications, small-to-medium sized databases and development environments. If you have workloads that run well on N1, but don’t require large instance sizes, GPUs or local SSD, consider moving them to E2. For all but the most demanding workloads, we expect E2 to deliver similar performance to N1, at a significantly lower cost.
Using resource balancing technologies developed for Google’s own latency-critical services, E2 VMs make better use of hardware resources to drive costs down and pass the savings on to you. E2 VMs place an emphasis on performance and protect your workloads from the type of issues associated with resource-sharing thanks to our custom-built CPU scheduler and performance-aware live migration.
You can learn more about how dynamic resource management works by reading the technical blog on E2 VMs.
At launch, we’re offering E2 machine types as custom VM shapes or predefined configurations:

We’re also introducing new shared-core instances, similar to our popular f1-micro and g1-small machine types. These are a great fit for smaller workloads like micro-services or development environments that don’t require the full vCPU.

E2 VMs can be launched on-demand or as preemptible VMs. They are also eligible forcommitted use discounts, bringing additional savings up to 55% for 3 year commitments. E2 VMs are powered by Intel Xeon and AMD EPYC processors, which are selected automatically based on availability.
E2 VMs are rolling out this week to eight regions: Iowa, South Carolina, Oregon, Northern Virginia, Belgium, Netherlands, Taiwan and Singapore; with more regions in the works. To learn more about E2 VMs or other GCE VM options, check out our machine types page and our pricing page.
The content below is taken from the original ( in /r/ Python), to continue reading please visit the site. Remember to respect the Author & Copyright.
https://youtu.be/ToK-5VwxhP4 (one minute video)
Reqman is a command-line based tool (available on all platforms), which let you test your rest apis, by describing your requests/tests in simple yaml files, with any text editors.
Writing tests is really easy, and suitable for non-tech people
Available on pypi .. available on github
DEMO: an online yaml/reqman editor/tester
BONUS: An online tool to convert your swagger/openapi3 definitions, or a postman collection, to reqman's yaml tests files.
Reqman helps me a lot, in my everyday work, to automate my non-regressions tests (TNR) on 100apis (with more than 2000 tests). And I'm pretty sure that It could help someone else.
The content below is taken from the original ( Download Reddit images in bulk with Reddit Image Grabber), to continue reading please visit the site. Remember to respect the Author & Copyright.

 Now and again, we all may want to download images from Reddit, but it can be time-consuming when its tie to go through a ton of pages on the website. Luckily for you, there is an app out there that […]
Now and again, we all may want to download images from Reddit, but it can be time-consuming when its tie to go through a ton of pages on the website. Luckily for you, there is an app out there that […]
This post Download Reddit images in bulk with Reddit Image Grabber is from TheWindowsClub.com.